The Chinese video surveillance company Hikvision’s over 80,000 cameras were exposed online due to a critical defect so let’s discuss all the details of this security issue.
The company is already familiar with this flaw, and that’s why last year, in September, it addressed this issue through a firmware update. At the same time, this update was aimed at more than 280,000 installed camera owners.
Hikvision Users Should Know This Flaw
This update is named CVE-2021-36260, and the prior firmware allows hackers to easily exploit the cameras with the dispatch of a crafted message to the vulnerable web server, which is directly linked to the camera.
According to a cyber security firm Cyfirma, these 80 thousand are owners who haven’t installed the firmware update Hikvision released last year.
Besides, Cyfirma also mentioned that 2,300 organizations across 100 countries mainly use these without security update systems, and also, they might be left with default passwords while setting up.
Two exploits were published in the past regarding it, first in October 2021 and another in February 2022, revealing proof that high-skill-level hackers are sharing it in their forums.
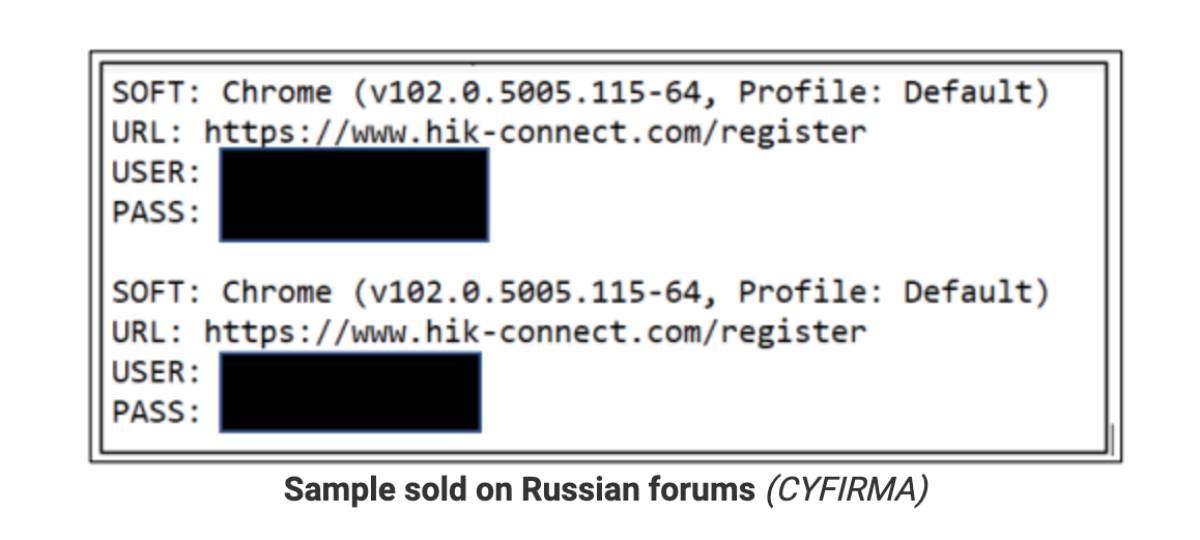
Their report also stated, “Specifically in the Russian forums, we have observed leaked credentials of Hikvision camera products available for sale”.
Additionally, in December last year, a Mirai-based Botnet came up that used this exploit to make it more extended by adding those systems into a DDoS throng.
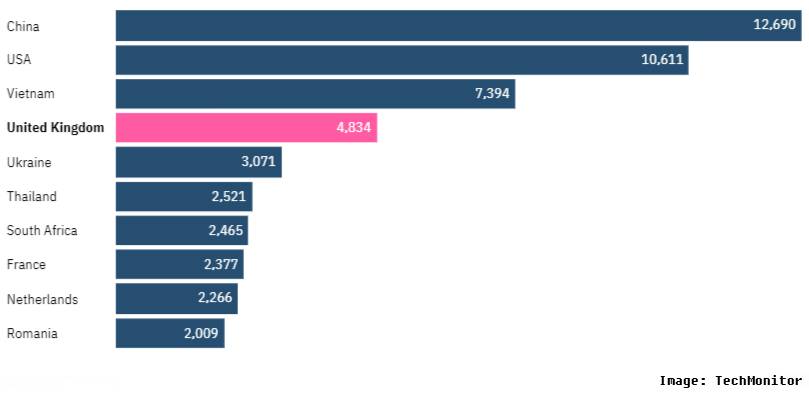
With all that, Cyfirma’s research has also found the top 10 countries that haven’t unpacked the security update for their systems, and it highlights China and the US might face more exploitation than other countries.
As you can see, the whole chart in the above image after these big countries also includes some major European countries such as the UK, Ukraine, and France.
While the company has already responded many times and said, “you should download the latest firmware for your device from the global firmware portal”.